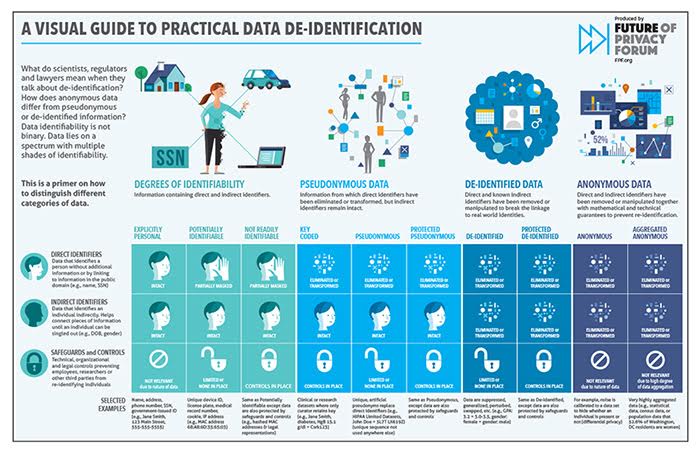
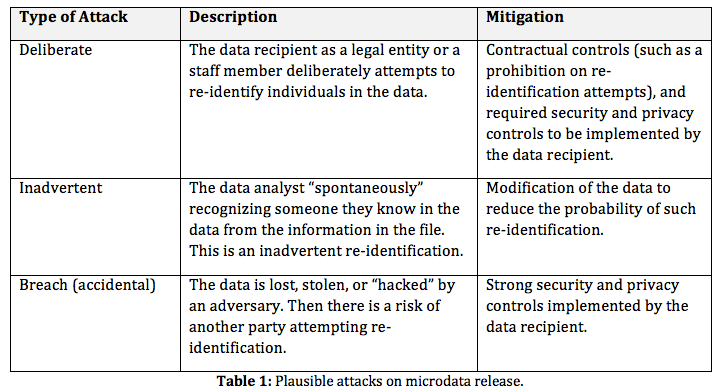
Factors/characteristics identifying the four data collection domains... | Download Scientific Diagram

Identifying Specific Data Needs - Data Module #3 - Finding & Collecting Data for Your Research - All Guides at Macalester College

Detecting Personal Data within API Communication Using Deep Learning | by Gianluca Brigandi | Towards Data Science
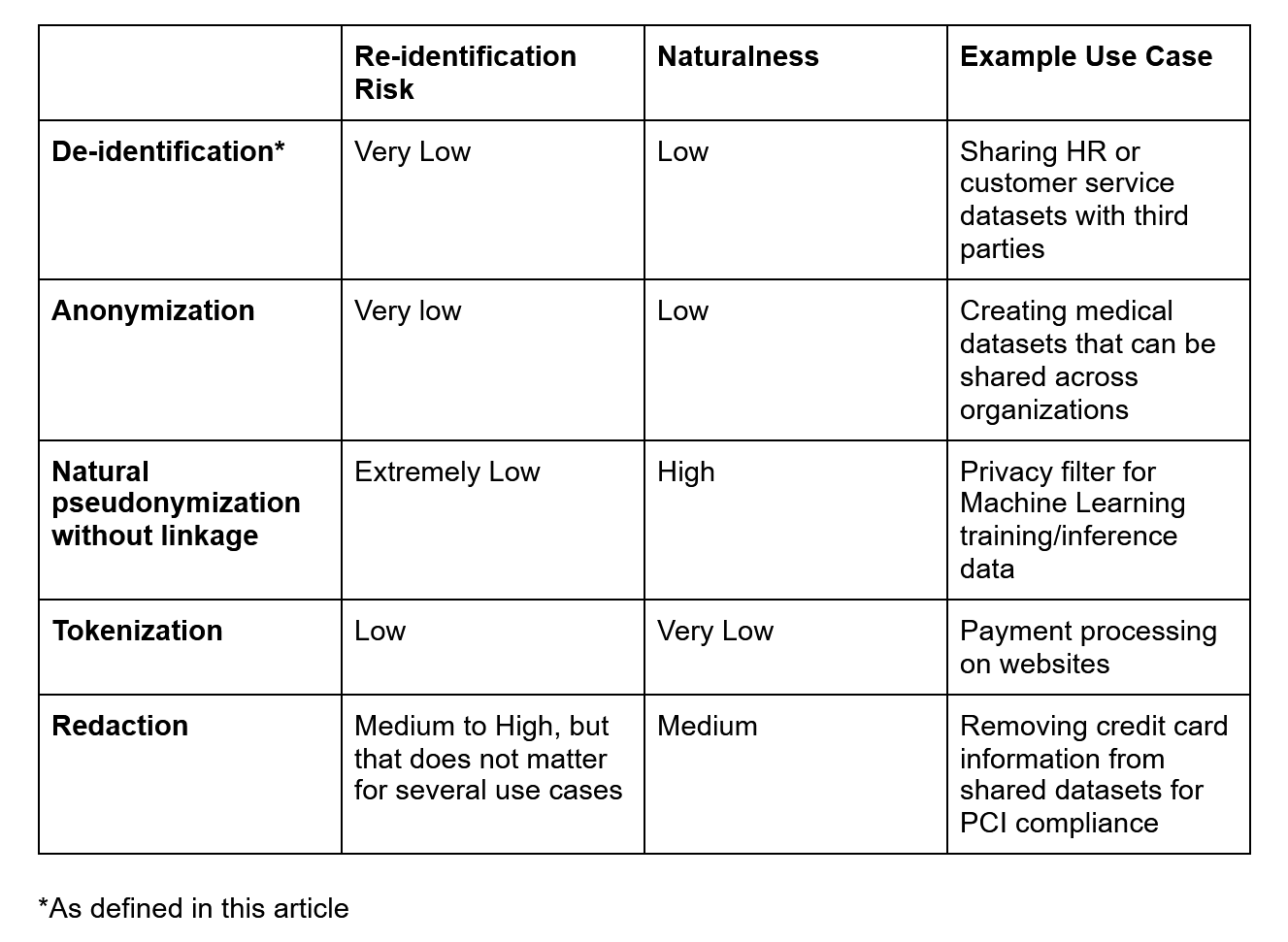
Demystifying De-identification. Understanding key tech for data… | by Patricia Thaine | Towards Data Science

Pediatric History Brenda Beckett, PA-C. History Identifying Data –name/parent's name –date of birth/age –sex/race Source (parent and/or child) –Reliability. - ppt download