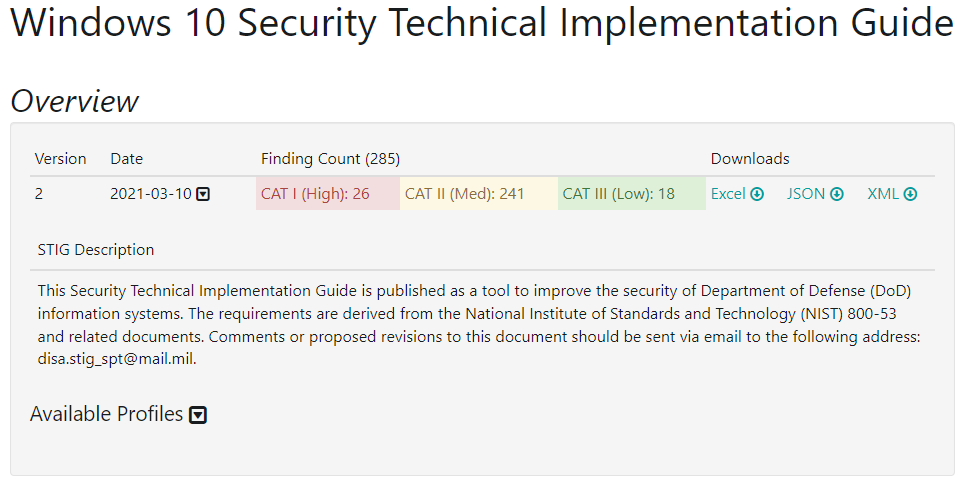
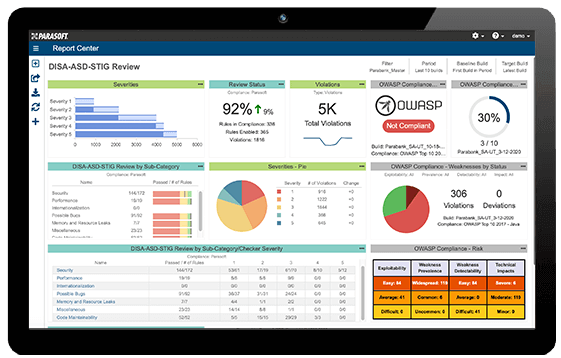
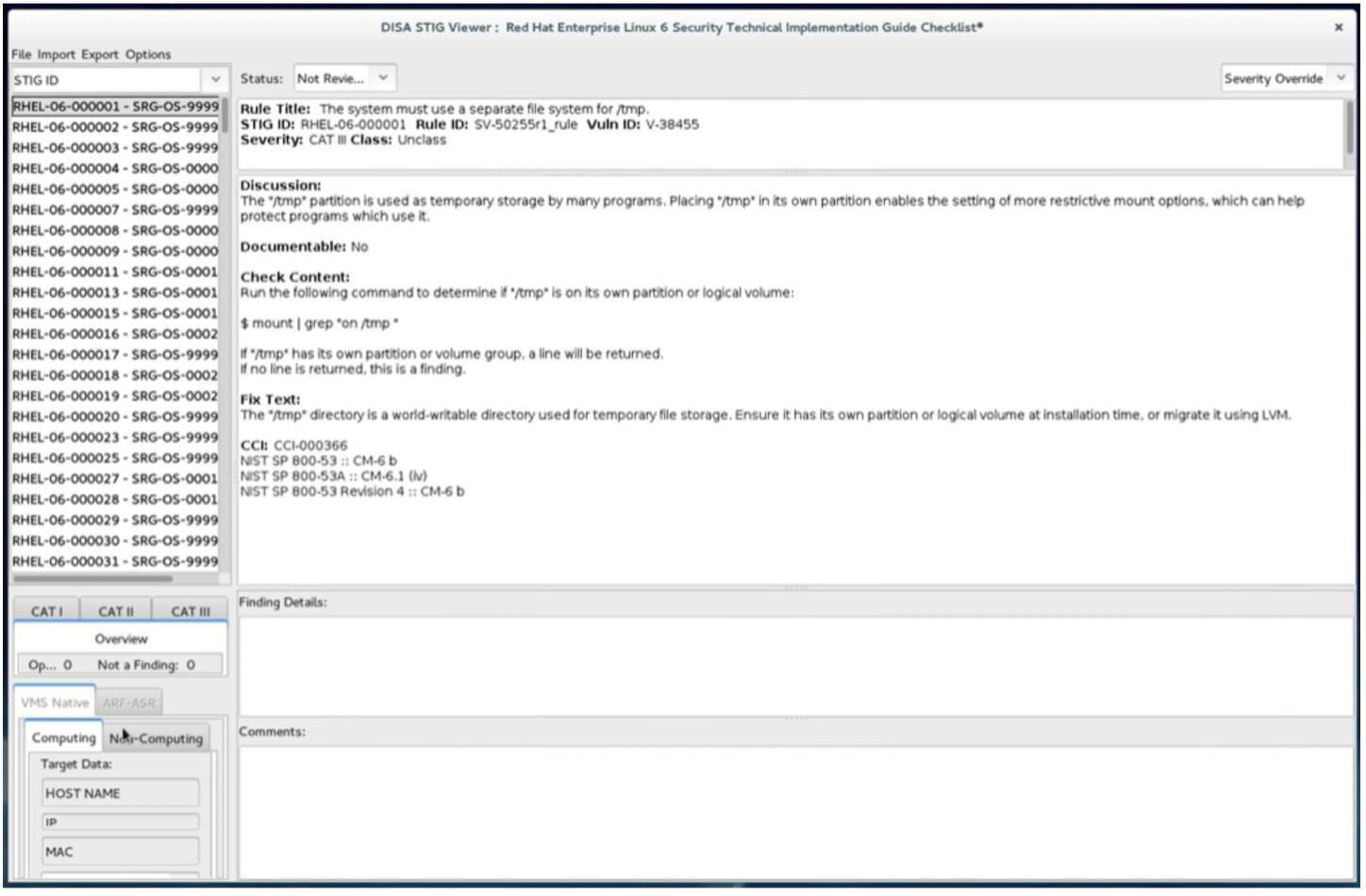
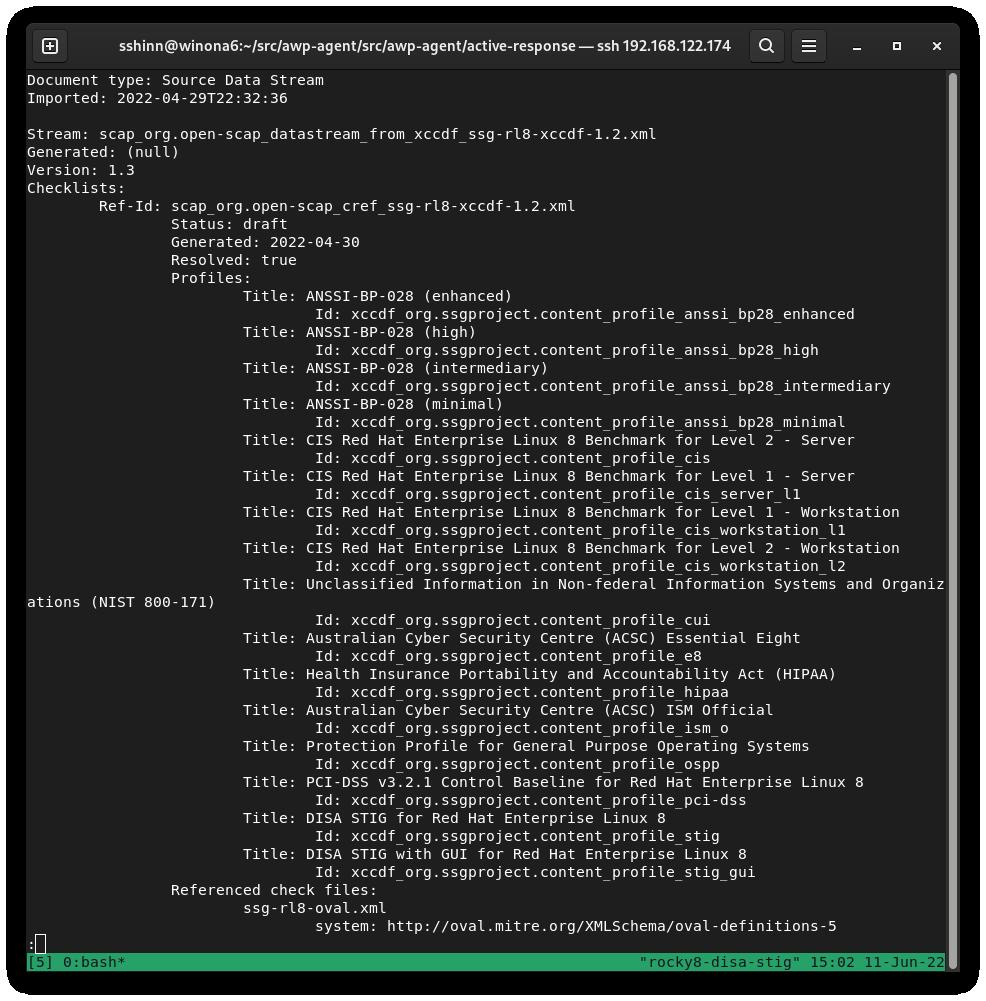
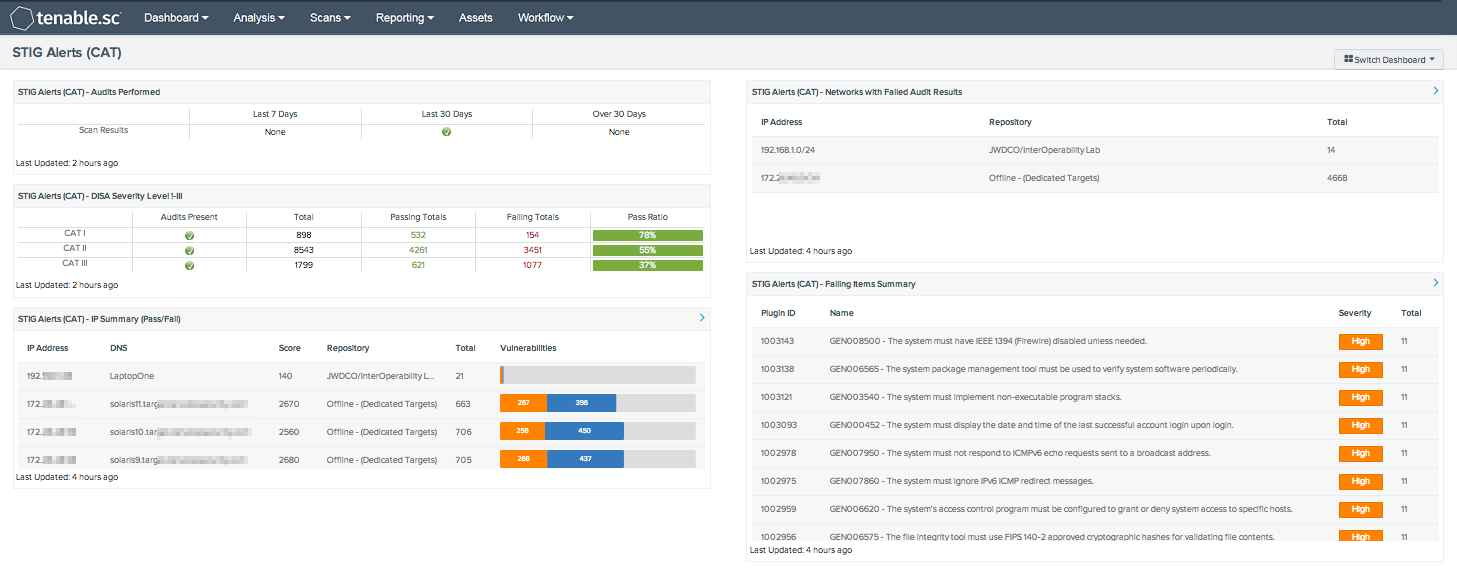
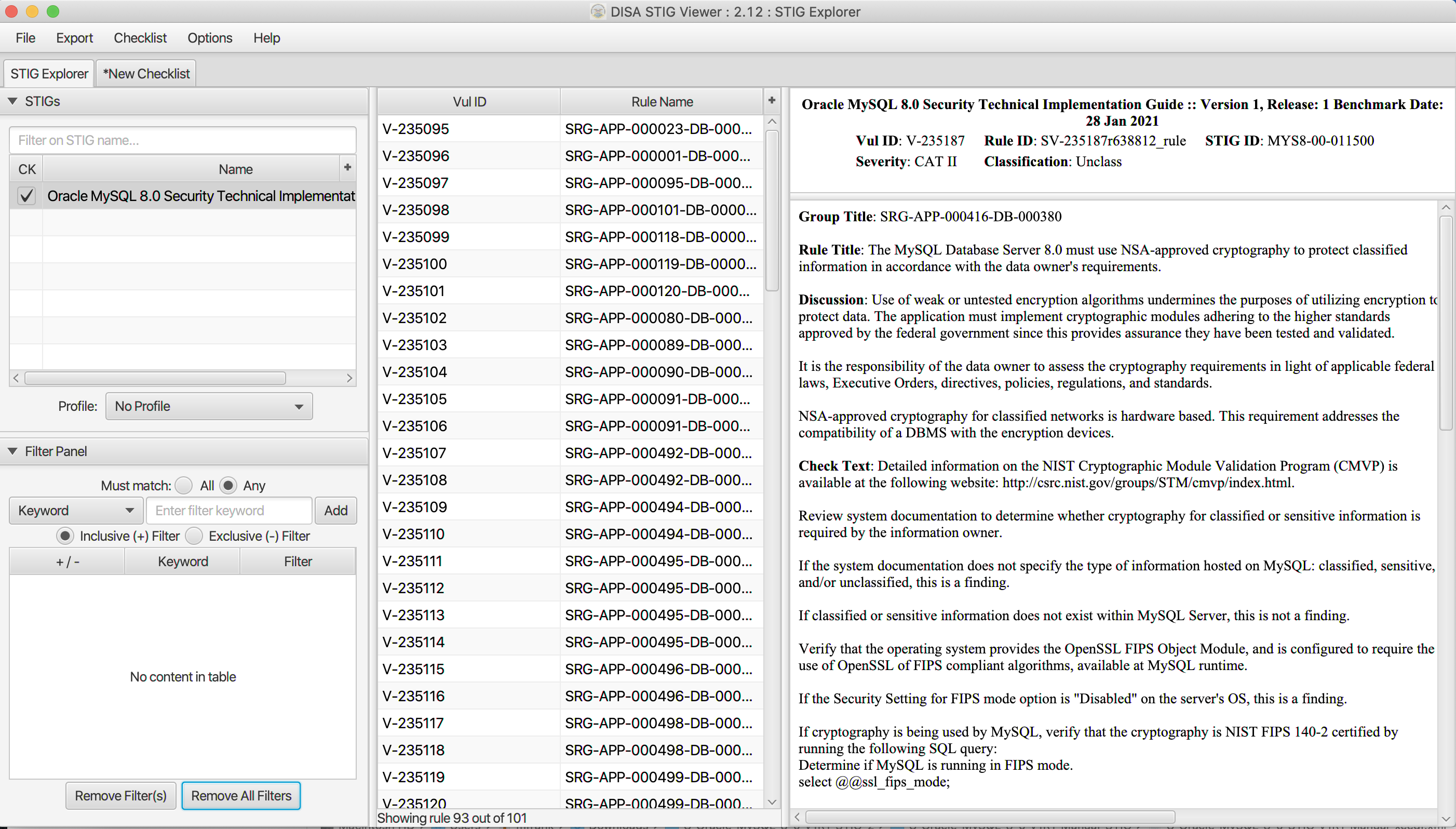
How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems

How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems

Quickly build STIG-compliant Amazon Machine Images using Amazon EC2 Image Builder | AWS Security Blog